Oracle Risk Management and Compliance
Oracle Risk Management and Compliance

Automate advanced security and transaction monitoring to strengthen financial controls, ensure separation of duties (SoD), stop fraud, and streamline audit workflows.
Additional information
Related Products:

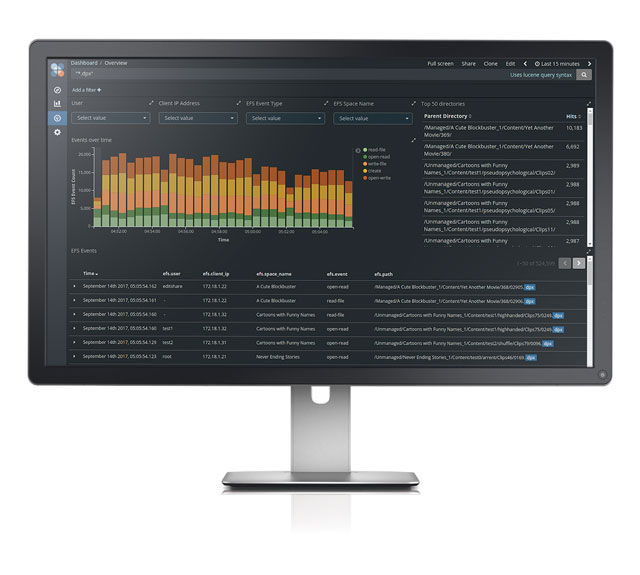
EditShare EFS File Auditing


Anti-Piracy Solution


Anti-piracy infringement Takedown services


BaishanCloud Cloud Shield


Oracle Risk Management and Compliance


DoveRunner Content Security


MediaPulse Managed Cloud
EditShare EFS File Auditing
Anti-Piracy Solution
MainStreaming’s cutting-edge Anti-Piracy solutions allows media companies to safeguard video content across live and on-demand streams.
With real-time updates, dynamic detection of piracy threats, and advanced actions like blocking and throttling, our system creates pirates face constant roadblocks. Sophisticated algorithms monitor abnormal consumption patterns, while customizable management tools offer enhanced control over network policies.
This solution allows broadcaster, OTT platforms and rights owners to stay ahead of evolving piracy tactics to not only block access but also frustrate pirates, securing premium content. MainStreaming Anti-Piracy tool comes with a full set of Analytics and can be instructed to either provide a report of ongoing threats without taking action, or to both report and respond. Reactions can be fully customized and tailored based on the origin of the threat and specific threat categories.
Anti-piracy infringement Takedown services
- Our inhouse trained manual resource enables us to be nimble and work around technical challenges and changes in the online landscape in ways which automation simply doesn’t allow for.
- Our expertise allows us to build processes that enable our services to scale so that we have a greater impact.
- Our in-house investigators and anti-piracy experts have extensive and specialist knowledge of the internet and know the most effective way to cause disruption
BaishanCloud Cloud Shield
In the process of digital transformation, an increasing number of enterprises are devoting more resources to building their web applications and APIs to meet their growing business needs. While it may provide users with the ability and flexibility to interact with their sites, enterprises often fall victim to malicious cyber-attacks which could lead to such devastating results as server downtime, user data breach, compromised database, and more. Baishan Cloud Shield security solution fully addresses the security issues of customers and provides them with comprehensive security protection on the edge. Baishan’s Cloud Shield security solution provides broad protection for websites and applications against all types of sophisticated attacks, including DDoS, web application, and direct to origin attacks, leveraging its high-bandwidth, globally distributed network with multiple tiered architectures. It is deployed across Baishan’s edge platform, which has more than 600 points-of-presence (PoP) globally across all major continents, so customers do not need to sacrifice performance for protection.
Product Highlights
Security at the edge with 50+Tbps capacity globally. The AI-powered solution to provide up-to-date threat mitigation. Tight integration with cloud acceleration service. Self-configurable rulesets with real-time logging. Dedicated security research team to identify threats
Always-on DDoS Protection
Each PoP in Baishan’s globally distributed network is built with proprietary DDoS mitigation technologies. With 50+ Terabits-per-second (and growing) capacity, it is a safety net to absorb DDoS attacks on Layer 3 and Layer 4 while allowing the good traffic to pass through. It protects against distributed attacks such as Ping floods, ICMP floods, web sockets attack, transaction floods, resource exhaustion, and UDP abuse. Baishan also works closely with local Internet Service Providers to strategically deploy three-tiered scrubbing centers around the world for more substantial distributed attacks. Each location within the three-tiered scrubbing center can scrub up to 1 Terabits-per-second of DDoS traffic. For application level (Layer 7) attacks, Baishan offers customizable edge rules to protect the network. Our distributed edges will inspect the entire HTTP/HTTPS requests and filter them based on request attributes such as IP addresses, cookies, or headers.
Web Application Firewall at the Edge
Baishan's Cloud Shield WAF protects applications from malicious attacks designed to compromise web servers. It is built on Baishan's globally distributed network with an AI-powered analytical engine to automatically and continuously detect and categorize new threats and vulnerabilities as they emerge (including the zero-day exploits) and to create new WAF rules to mitigate the attack. On top of the rulesets created and maintained by Baishan, this product also incorporates rulesets from open source communities such as OWASP, Common Vulnerabilities and Exposures (CVE), and Chinese National Vulnerability Database (CNVD). The WAF protects against common attacks including injection attacks, cross-site scripting, sensitive data exposure, website tempering, directory traversal attack, and more. Baishan’s WAF also offers keyword flagging features, specifically for websites and applications with user-generated content, so customers can detect and replace any keyword to provide necessary content regulation and to avoid censorship. WAF rules can be customized and managed in real-time via Portal or API based on customers’ unique request scenarios. All traffic going through WAF is logged and analyzed for customers to have 100% visibility into their traffic.
TLS Termination at Edge
Protecting the identity and the integrity of a website requires strong encryption. Baishan supports Transport Layer Security (TLS) to enables end-to-end HTTPS connections between clients and origin server, preventing man-in-the-middle attacks, packet sniffing, and more. TLS connections are encrypted and terminated at Baishan’s globally distributed edge, closer to the end-users, which reduces the latency. Baishan supports TLS 1.1, TLS 1.2, and the latest TLS1.3 with customizable cipher suites.
Bot Management
Undetected malicious bots can damage a website's reputation, steal sensitive information, and negatively impact business revenue. Baishan’s Cloud Shield offers comprehensive bot management built with a machine-learning engine to dynamically detect and block malicious bots. It protects the application against web scrappers, malicious API connections, content tampering, user-specific information stuffing, and more. At the same time, it has a configurable whitelist to allow good bots, such as those belonging to search engines, to pass through to the site. Cloud Shield is built with a sophisticated mechanism to automatically detect malicious bots from the good bots and also allows the customer to customize mechanisms, such as CAPTCHA and JavaScript challenge, to filter away the requests from malicious bots, as an additional layer of protection.
Real-time Logging and Analysis
Baishan’s Cloud Shield gives customer full insight into their request profiles, security events, and provide real-time analysis and notifications. Customers can monitor threats and attacks with trend analysis in Portal or consume the statistical data via API to understand the traffic in order to take the most appropriate security measures to protect the websites. Near real-time logging is available and can be pushed to any log analysis platform customer prefers.
24/7 Global Support with Security Monitoring
Baishan’s Global Support is available 24/7 to assist customers with mitigating an existing attack or implementing preventative measures for future attacks. Baishan’s security experts conduct daily threat monitoring with vulnerability analyses of new threats, monitor industry bulletin boards for new threats and vulnerabilities, and creates new security rules that provide the most up-to-date web application protection.
Oracle Risk Management and Compliance
DoveRunner Content Security
Real-time threat detection and analytics
Runtime Application Self‑Protection (RASP), anti-tampering, anti-reverse engineering
Code obfuscation and encryption on Android/iOS
Fraud prevention to safeguard sensitive financial, gaming, retail, ride-hailing and healthcare apps doverunner.com
2. Content Security
Multi‑DRM licensing support (Apple FairPlay, Google Widevine, Microsoft PlayReady, Huawei Wiseplay)
Forensic watermarking for traceability
Anti-piracy tools including live-stream restream detection and distributor watermarking
Packaging, license service, andSDKs for easy integration
3. Combined “Complete Security” Offering
DoveRunner offers an end-to-end platform merging mobile app and content security for maximum protection and regulatory compliance.
MediaPulse Managed Cloud
Xytech’s Microsoft Azure Cloud is safe, secure and reliable with fifty compliance offerings. Linking MediaPulse with Azure Cloud creates a highly efficient platform for MediaPulse deployments and simultaneously lowers costs.
There are two significant advantages in Xytech’s Azure Cloud offering. First, Azure has fully integrated and managed Microsoft SQL Server database and secondly, your instance is managed by the MediaPulse experts at Xytech, reducing costs and increasing user satisfaction.
These advantages result in higher efficiency, better service and lower costs, while increasing uptime and protecting your data. The MediaPulse Managed Cloud is the premier choice for your facility management system.
Shared instances are available in both United States and Europe. Private instances are available in many countries across the globe. Azure is a trusted cloud provider for United States government institutions and includes a FedRAMP High authorization.
Benefits and Features
- Microsoft SQL database managed by Azure
- Backups occur every 5 minutes
- Proactive database analysis
- Advanced Azure security
- Private database instance
- Geo-Replication for High Availability
- Encrypted data transfer
- API integration capabilities for any cloud or on-premises system
- Three levels of managed services
- Complete product support for the Xytech software
- Managed product upgrades
- Worldwide private cloud available
- Web and mobile compatible
- Single Sign-On (SSO) and OpenID Connect authentication
- 24×7 access and support



